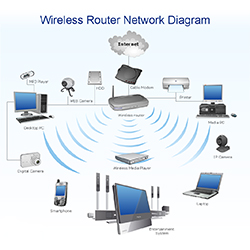
Wireless Network
A wireless transmission method is a logical choice to network a LAN segment that must frequently change locations. The following situations justify the use of wireless technology:
- To span a distance beyond the capabilities of typical cabling,
- To provide a backup communications link in case of normal network failure,
- To link portable or temporary workstations,
- To overcome situations where normal cabling is difficult or financially impractical, or
- To remotely connect networks.
Developers need to consider some parameters involving Wireless RF technology for better developing wireless networks:
- Frequency trends
- Operating range
- Sensitivity and data rate
- Network topology and node intelligence

Fiber Optic Network
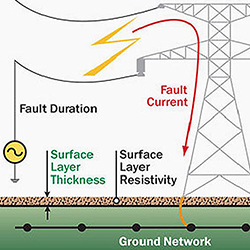
Power Earthing

Power protection devices
You may need a different power-protection strategy--either a one-on-one approach, a clustered system, integrated protection, or floor-by-floor protection facility-wide--depending on the type of facility and kind of network. Power protection used to be as simple as placing all sensitive equipment inside a "glass house" that was connected to a single power-protection source, such as an uninterruptible power supply (UPS). Today, with computers migrating from the raised-floor data center into telecommunications closets and even open work areas, power-protection strategies must deal with a much more complicated situation.
First, power-protection equipment must contend with an increasingly wide range of system configurations. Servers, workstations, routers, hubs, bridges and other sensitive components must all be taken into consideration.
Second, as computer-based systems become more integral to telecommunications operations, even a minor power problem can have catastrophic effects--from absorbing a half day of an employee`s time for reentering data to sustaining a costly production loss because an industrial machine controller`s part program was erased by a power glitch and the machine produced scrap. In many telecommunications applications (e.g., computerized order processing) a power problem can completely shut down operations. o serve a user`s needs, the UPS, which is the main component in most power-protection systems, must be able to handle different types of power inputs, including imperfect power from the electric utility, direct current (DC) power from batteries, the variable output of standby generators, surges and sags from inside the building, and even harmonics from within the computer network. Contemporary UPS systems are available in a variety of configurations to meet these multiple needs, but they can generally be classified into one of three types of technologies: online, offline or line interactive.

RFID Readers
In a basic RFID system, tags are attached to all items that are to be tracked. These tags are made from a tiny tag-chip, sometimes called an integrated circuit (IC), that is connected to an antenna that can be built into many different kinds of tags including apparel hang tags, labels, and security tags, as well as a wide variety of industrial asset tags. The tag chip contains memory which stores the product's electronic product code (EPC) and other variable information so that it can be read and tracked by RFID readers anywhere.
An RFID reader is a network connected device (fixed or mobile) with an antenna that sends power as well as data and commands to the tags. The RFID reader acts like an access point for RFID tagged items so that the tags' data can be made available to business applications.

CNIC Readers

Thermal Printers

Card Printer

E-Tag

LED Signs
